Which one of the following fields of an IP header is NOT modified by a typical IP router?
1. Data Link layer (i) The lowest layer whose function is to activate, deactivate and maintain the circuit.
2. Physical layer (ii) Perform routing and communication.
3. Presentation layer (iii) Detection and recovery from errors in transmitted data.
4. Network layer (iv) Concerned with the syntax of the data.
I. Send the data over the Internet to the computer in New Delhi. The data rate for transmitting information across the Internet from his house to New Delhi is 1 MBps
II. Copy the data over to a set of disks, which he can do at 100 MBps. Then rely on the Indian Postal Service to send the disks by mail, which takes 5 days.
Which of the following is correct?
Identify the interval of the time when TCP congestion avoidance is operating the second time and what is the initial value of threshold respectively.
1. Link state algorithms: Computes the least-cost path between source and destination using complete, global knowledge about the network.
2. Distance-vector routing: The calculation of the least-cost path is carried out in an iterative, distributed manner. A node only knows the neighbour to which it should forward a packet in order to reach the given destination along with the least-cost path, and the cost of that path from itself to the destination.
a. Host A is sending Host B a large file over a TCP connection. Assume Host B has no data to send Host A. Host B will not send acknowledgements to Host A because Host B cannot piggyback the acknowledgements on data.
b. Suppose Host A is sending a large file to Host B over a TCP connection. If the sequence number for a segment of this connection is m, then the sequence number for the subsequent segment will necessarily be m + 1.
c. Suppose Host A sends one segment with sequence number N and X bytes of data over a TCP connection to Host B. In this same segment the acknowledgement number is necessarily N + X.
1. The first group has 32 customers; each needs 256 addresses.
2. The second group has 64 customers; each needs 128 addresses.
3. The third group has 128 customers; each needs 64 addresses.
After designing the subblocks and giving the slash notation for each subblock. How many addresses are still available after these allocations?
(i) Another ICM error message.
(ii) An IGMP Message of any kind.
(iii) Any fragment is other than the first fragment from a fragmented IP datagram.
(iv) A datagram with TTL exceeds.
Destination
|
Subnet Mask
|
Interface
|
154.126.0.0
|
255.255.0.0
|
I - 0
|
154.126.64.0
|
255.255.224.0
|
I -1
|
154.126.68.0
|
255.255.255.0
|
I - 2
|
154.126.68.64
|
255.255.255.224
|
I - 3
|
A packet bearing an estimation IP address is 154.126.68.128 arrives at the router.
On which interface will it be forwarded?
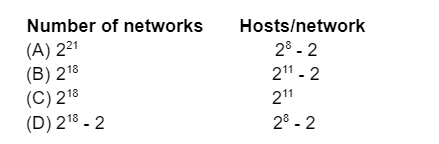
Table - I
1. An algorithm for digitally signing data with a private key such that anyone with possession of the corresponding public key can verify the signature.
2. A symmetric-key algorithm for ensuring that a message has tampered.
3. The security goal of ensuring that a message arrives at the recipient is identical to what the sender transmitted.
4. Standardized symmetric key encryption algorithm.
Table - II
What is the fragment offset for the third packet received by destination?